Table of Contents
In the digital age, where organizations rely heavily on technology to conduct their operations, the threat landscape for cyberattacks has grown more complex and sophisticated. As a result, having the best IT infrastructure is no longer a luxury but a necessity to counter cyber threats effectively.
With ever-increasing ransomware attacks and supply chain vulnerabilities, it's imperative to empower your security team with AI and machine learning and leveraging advanced techniques to fortify your defenses. With the rise of remote work and consequential, Bring Your Own Device (BYOD) policies; safeguarding critical assets and sensitive data is paramount for providing optimal customer experiences and minimizing damages has necessitated real-time data protection against potential threats.
In this extensive discussion, we’ll delve into the advantages that organizations can gain from employing robust cyber security services and practices within their IT infrastructure and the role Rapid Application Development plays in preventing cyberattacks.
Part I: The Advantages of Robust IT Infrastructure in Cyber Security Threat Detection and Mitigation
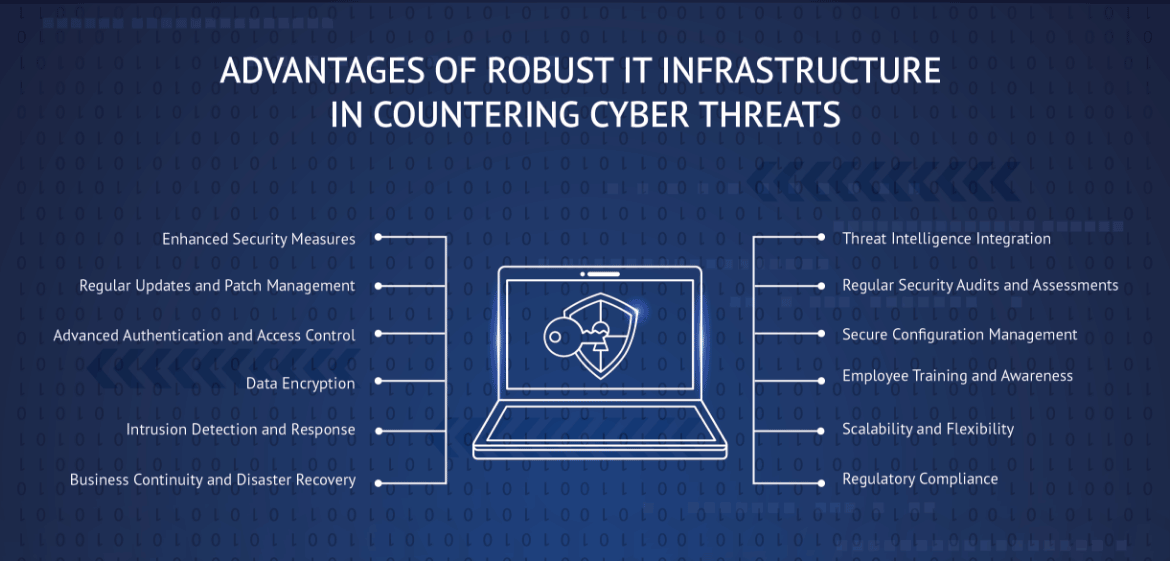
- 1. Enhanced Security Measures: Robust IT infrastructure includes security layers such as firewalls, intrusion detection systems, and antivirus software. These measures act as a strong defense against various cyber threats, providing a secure perimeter for an organization’s digital assets.
- 2. Regular Software Updates and Patch Management: Organizations with robust IT infrastructure have established processes for regular updates and patch management software. They ensure that software and hardware vulnerabilities are addressed promptly, reducing the potential attack surface for cybercriminals.
- 3. Advanced Authentication and Access Control: Strong authentication methods, including multi-factor authentication (MFA), are an integral part of robust IT infrastructure. Access control mechanisms ensure that only authorized users can access sensitive systems and data, preventing unauthorized entry.
- 4. Data Encryption: Encryption of data at rest and in transit is a hallmark of sound IT infrastructure. This safeguards data from interception and compromise, even if attackers gain access to the network.
- 5. Intrusion Detection and Incident Response: Robust IT infrastructure incorporates intrusion detection and response systems that monitor network traffic for suspicious activity. In case of a breach, automated responses can quickly contain the threat.
- 6. Business Continuity Disaster Recovery: Well-structured IT infrastructure includes comprehensive business continuity and disaster recovery plans. These plans ensure that organizations can continue their critical operations in the event of a cyber incident, reducing downtime and losses.

- 7. Threat Intelligence Integration: Organizations with robust IT infrastructure integrate threat intelligence feeds to stay informed about emerging threats and vulnerabilities. This proactive approach helps in pre-emptive mitigation.
- 8. Regular IT Security Audit and Assessments: Periodic IT security audits and assessments are conducted to identify vulnerabilities and weak points in the IT infrastructure. Remediation measures are taken promptly to address any issues discovered.
- 9. Secure Configuration Management: Secure configuration management ensures that systems are set up following IT security best practices. This reduces the chances of misconfigurations that can be exploited by cybercriminals.
- 10. Employee Training and Awareness: Organizations with robust IT infrastructure invest in cybersecurity training and awareness programs for their employees. This educates the workforce on recognizing and responding to potential threats effectively.
- 11. Scalability and Flexibility: Scalable infrastructure can adapt to the evolving threat landscape and changing business needs. Organizations can quickly deploy additional security measures or resources as required.
- 12. Cybersecurity Regulatory Compliance: Many industries have regulatory requirements for cybersecurity. Robust IT infrastructure ensures that organizations can comply with these regulations, avoiding legal and financial penalties.
Conclusion
In today's cyber landscape, robust IT infrastructure and rapid application development are indispensable for mitigating threats effectively. These measures offer enhanced security, proactive threat detection, and resilience against cyber incidents. By integrating advanced technologies and fostering a culture of cybersecurity awareness, organizations can navigate the digital realm with confidence, securing their future in an evolving threat landscape.
Explore other articles:




