Table of Contents
Your security team just identified a breach. The initial compromise happened 72 hours ago. The warning signs were there: unusual database queries, elevated API traffic, anomalous login patterns. Each signal appeared in a different monitoring dashboard. No single team saw the complete picture. No system connected the dots.
This scenario plays out repeatedly across enterprises managing 10, 15, or 20+ monitoring dashboards. Application performance monitoring in one tool. Infrastructure metrics in another. Security logs in a third. Cloud provider dashboards for each environment. Network monitoring separately. Each tool generates alerts. Each alert lands in a different queue. Each queue belongs to a different team.
The result? Alert fatigue, delayed incident response, and dangerous security blind spots. Your organization has comprehensive visibility into individual systems but lacks the unified intelligence needed to identify threats that span multiple domains.
Unified monitoring addresses this fundamental gap by correlating signals across all operational telemetry into a single, AI-driven intelligence layer that surfaces what matters and automatically assigns clear ownership.
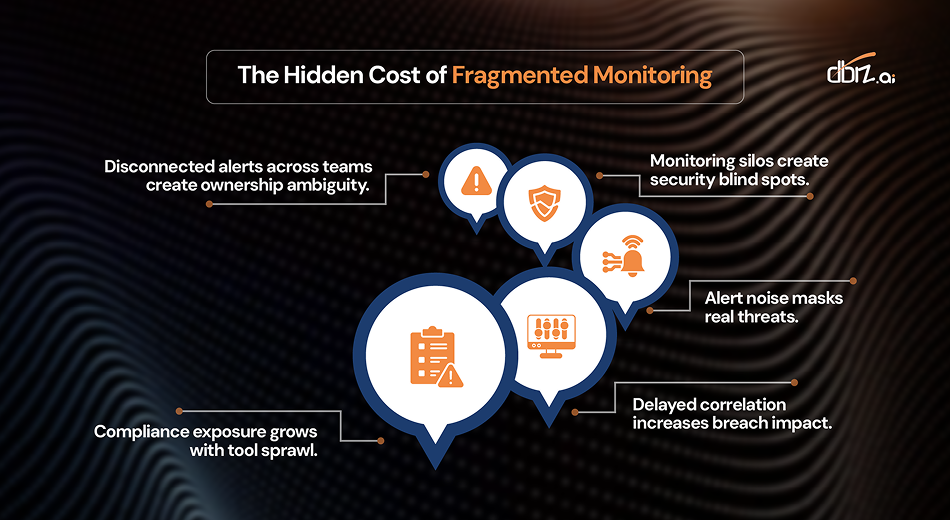
The Hidden Cost of Fragmented Monitoring
Most enterprises evolved their monitoring infrastructure organically. Infrastructure teams adopted tools for server metrics. Application teams deployed APM solutions. Security teams implemented SIEM platforms. Cloud migrations added native monitoring from AWS, Azure, and GCP. DevOps teams introduced container monitoring. Network operations maintained their legacy tools.
Each decision made sense in isolation. Together, they created operational fragmentation with serious consequences:
Disconnected alerts across teams create ownership ambiguity. When an incident involves application latency, database performance, and network congestion simultaneously, which team owns the response? By the time teams coordinate, customers are already affected and SLAs are breached.
Alert noise masks real threats. Individual monitoring tools generate thousands of alerts daily. Most are false positives or low-priority events. Critical signals indicating coordinated attacks or cascading failures get lost in the noise. Security teams spend hours triaging alerts that should have been automatically correlated and prioritized.
Monitoring silos create security blind spots. A sophisticated attack rarely triggers alarms in a single system. Attackers exploit the seams between monitoring domains. The login anomaly appears normal in identity logs. The data exfiltration looks like routine API traffic. The lateral movement blends with legitimate internal communications. Only when correlated do these signals reveal the attack pattern.
Delayed correlation increases breach impact. Manual correlation across dashboards takes time. Security teams must access multiple systems, export data, analyze relationships, and piece together the timeline. Meanwhile, the breach progresses. Every hour of delayed detection increases the scope of compromise and the cost of remediation.
Compliance exposure grows with tool sprawl. Audit requirements demand complete visibility into security events and operational anomalies. Fragmented monitoring creates gaps in audit trails, inconsistent log retention policies, and incomplete incident documentation. Demonstrating compliance becomes increasingly difficult and expensive.
The cost extends beyond operational inefficiency. According to IBM's 2023 Cost of a Data Breach Report, the average time to identify and contain a breach is 277 days. Fragmented monitoring directly contributes to these delays by hiding correlations that would accelerate detection.
Why Dashboards Alone Don't Create Security
Having visibility into your systems feels like having security. It creates a false sense of control. You can see server CPU utilization, application response times, failed login attempts, and network bandwidth consumption. Dashboards display real-time data with impressive visualizations.
But visibility without intelligence is dangerous.
Static thresholds can't detect behavioral anomalies. Traditional monitoring triggers alerts when metrics cross predefined thresholds. CPU above 80%, memory above 90%, error rate above 5%. These thresholds miss subtle degradation patterns and contextual anomalies. A login from an unusual location might not exceed any threshold but could indicate credential compromise. A gradual increase in outbound data transfer over weeks might stay below alerting thresholds while exfiltrating terabytes of sensitive information.
Human-dependent triage creates response bottlenecks. Even when monitoring tools detect anomalies, human operators must investigate, correlate related events, determine severity, and assign ownership. This manual process introduces 20-45 minute delays in the best case. For complex incidents spanning multiple systems, investigation can take hours. Security threats don't wait for human analysis.
The detection-to-response gap widens with complexity. Modern enterprise environments include on-premises infrastructure, multiple cloud providers, containerized applications, serverless functions, SaaS platforms, and third-party integrations. Each layer generates telemetry. Each integration creates new attack surfaces. The gap between detecting an anomaly in one layer and understanding its business impact across the entire stack continues to grow.
Attackers actively exploit monitoring fragmentation. Sophisticated threat actors understand enterprise monitoring architectures. They conduct reconnaissance to identify monitoring gaps. They distribute attack activities across systems to avoid triggering correlated alerts. They operate at speeds that exploit the delay between detection and response. A unified observability platform closes these gaps by providing continuous correlation across all telemetry sources.
Fragmented ownership increases mean time to detect and respond. When an incident requires coordination between infrastructure, application, security, and network teams, communication overhead dominates response time. Each team views the incident through their monitoring lens. Conflicting data interpretations lead to circular discussions while the issue escalates. Clear ownership assignments based on business impact and technical scope become impossible without unified context.
The Unified AI-Driven Approach
True unified monitoring goes far beyond consolidating dashboards into a single pane of glass. It requires fundamental changes to how telemetry is collected, processed, correlated, and acted upon.
DBiz.ai's approach to unified monitoring centers on several core capabilities:
Centralized telemetry ingestion across all domains. Application logs, infrastructure metrics, distributed traces, security events, cloud provider APIs, container orchestration data, network flows, and business KPIs all flow into a unified data lake. This creates a complete operational graph showing relationships between services, infrastructure, users, and business processes that fragmented tools cannot reveal.
AI-powered event correlation eliminates noise. Machine learning models analyze incoming telemetry to identify meaningful patterns and suppress irrelevant alerts. The system learns normal behavior for each service, user, and process. It detects deviations from these baselines and groups related anomalies into coherent incidents rather than generating hundreds of individual alerts.
Cross-domain anomaly detection surfaces hidden threats. Unified monitoring applies behavioral analysis across infrastructure, applications, and security domains simultaneously. It identifies attack patterns that span multiple systems. A credential compromise attempt, followed by privilege escalation, followed by lateral movement, followed by data access generates signals in different monitoring domains. Unified AI-driven analysis connects these dots automatically.
Root-cause grouping replaces alert storms. When a database performance issue triggers application latency, which triggers user-facing errors, which triggers automated scaling, which triggers cloud cost alerts, fragmented monitoring generates five separate incident tickets. Unified monitoring understands the causal chain and creates a single incident with complete context and clear root cause identification.
Business-impact prioritization focuses teams on what matters. Not all incidents deserve the same response urgency. A test environment database failure differs fundamentally from a production payment gateway issue. Unified monitoring maps technical events to business services, revenue streams, and SLA commitments. It prioritizes incidents based on actual business impact rather than arbitrary severity classifications.
Signal enrichment provides actionable context. Each alert includes complete context: affected services, dependent systems, recent changes, relevant runbooks, historical incident data, and assigned owners. Engineers receive everything needed to respond effectively without manually gathering information from multiple systems.
The cost extends beyond operational inefficiency. According to IBM's 2023 Cost of a Data Breach Report, the average time to identify and contain a breach is 277 days. Fragmented monitoring directly contributes to these delays by hiding correlations that would accelerate detection.
DBiz.ai's approach to unified monitoring centers on several core capabilities:
ML-based pattern recognition learns from historical incidents to predict and identify similar patterns in real-time telemetry. Signal enrichment adds business context, service ownership, and dependency mapping to raw technical events. Ownership automation routes incidents to the correct teams based on service mapping and on-call schedules. Context-aware alert routing ensures alerts reach teams through appropriate channels with urgency aligned to business impact.
Organizations seeking to implement this approach can contact DBiz.ai to design a unified monitoring architecture tailored to their specific operational complexity and security requirements.
Streamlining Ownership and Response
Unified monitoring delivers operational value through clear ownership and accelerated response workflows.
Automatic service mapping establishes clear boundaries. The system continuously discovers services, their dependencies, their owners, and their business criticality. When an incident occurs, ownership assignment is immediate and unambiguous based on which service is affected and which team is responsible for that service.
Team-based routing eliminates handoff delays. Incidents route directly to the team with both the technical expertise and organizational authority to resolve the issue. No more triage meetings to determine who should respond. No more ticket reassignments as incidents bounce between teams. The right people receive the right information immediately.
Playbook automation handles well-understood scenarios. For common incident patterns with established remediation procedures, automated playbooks execute response steps without human intervention. Restarting failed services, scaling constrained resources, isolating compromised accounts, rotating exposed credentials. All while maintaining complete audit trails and notifying relevant stakeholders.
Policy-driven remediation ensures governance. Automation executes within guardrails defined by organizational policies. High-risk actions require human approval. Lower-risk remediations proceed automatically but remain reversible and logged. Security policies, compliance requirements, and change management procedures integrate directly into response workflows.
Reduced manual handoffs accelerate resolution. Traditional incident response involves multiple handoffs: from monitoring to triage, triage to assignment, assignment to investigation, investigation to remediation, remediation to validation. Each handoff introduces delay and information loss. Unified monitoring eliminates most handoffs by providing complete context and clear ownership from the moment of detection.
The measurable outcomes validate this approach:
Organizations implementing unified AI-driven monitoring report faster mean time to detect (MTTD) as correlation eliminates the delay between individual signal detection and threat recognition. Faster mean time to respond (MTTR) results from clear ownership, complete context, and automated playbooks. Reduced security exposure windows shrink as the gap between compromise and remediation compresses. Clear accountability emerges as every incident has assigned owners and documented response activities.
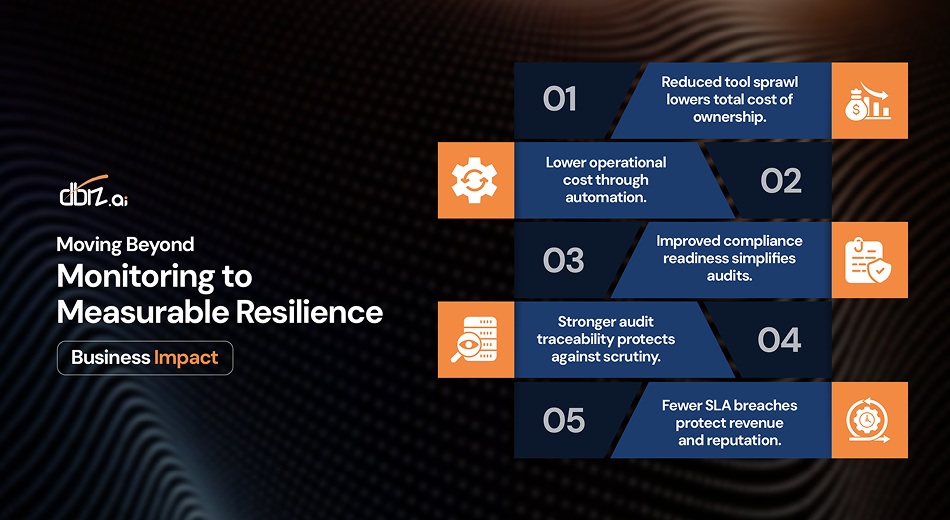
Business Impact: Moving Beyond Monitoring to Measurable Resilience
The business case for unified monitoring extends beyond operational efficiency to strategic resilience and risk reduction.
Reduced tool sprawl lowers total cost of ownership. Consolidating 15+ monitoring tools into a unified platform eliminates redundant licensing costs, reduces training overhead, and simplifies vendor management. Teams spend less time managing monitoring infrastructure and more time deriving value from operational intelligence.
Lower operational cost through automation. Manual alert triage, correlation, and incident routing consume significant engineering time. Unified AI-driven monitoring automates these activities, freeing teams to focus on proactive improvement rather than reactive firefighting. The labor cost savings alone often justify the investment.
Improved compliance readiness simplifies audits. Complete telemetry retention, unified audit trails, and comprehensive incident documentation satisfy regulatory requirements with less manual effort. Demonstrating compliance becomes a query against centralized data rather than a months-long evidence gathering exercise across fragmented systems.
Stronger audit traceability protects against scrutiny. When regulators, auditors, or legal teams request evidence of security controls, incident response, or change management, unified monitoring provides complete, correlated records. No gaps in visibility. No missing logs. No reconciliation challenges across inconsistent systems.
Fewer SLA breaches protect revenue and reputation. Faster detection and response directly reduce downtime duration. Business-impact prioritization ensures the most critical services receive immediate attention. Predictive analytics identify degradation before it violates SLAs. These capabilities translate directly to preserved revenue, maintained customer trust, and competitive advantage.
Real-world implementations demonstrate consistent metrics across industries:
Organizations implementing unified AI-driven monitoring report faster mean time to detect (MTTD) as correlation 35% reduction in alert noise as intelligent correlation eliminates redundant and low-value alerts. 40% faster incident ownership assignment through automatic service mapping and team-based routing. 50% improvement in cross-team collaboration as unified context eliminates conflicting interpretations and reduces coordination overhead.
Financial services organizations use unified monitoring to correlate fraud detection signals with transaction anomalies and infrastructure performance. Healthcare providers identify security incidents faster by correlating patient data access patterns with network behavior. E-commerce platforms protect revenue by detecting and responding to performance degradation before customers abandon purchases.
The strategic value compounds over time. As ML models learn from each incident, correlation accuracy improves. As teams build response playbooks, automation coverage expands. As business context enriches telemetry, prioritization becomes more precise. Unified monitoring evolves from a monitoring platform into a strategic resilience capability.
Organizations ready to eliminate monitoring fragmentation can start by unifying observability across their top business-critical services before expanding to comprehensive coverage.
Conclusion: The End of Reactive Operations
Dashboard fatigue is a symptom of a deeper problem. Fragmented monitoring creates operational silos, security blind spots, and response delays that modern enterprises cannot afford.
The solution requires more than consolidating dashboards. It demands unified telemetry ingestion, AI-driven correlation, cross-domain anomaly detection, automatic ownership assignment, and policy-driven automation. These capabilities transform monitoring from passive visibility into active intelligence that accelerates detection, clarifies ownership, and enables rapid response.
Security threats exploit the gaps between monitoring domains. Operational incidents cascade across system boundaries. Business impact extends beyond individual technical components. Unified AI-driven monitoring addresses these realities by providing complete context, intelligent prioritization, and clear accountability.
The organizations that will thrive in increasingly complex and hostile environments are those that move beyond monitoring individual systems to understanding the relationships between systems, the patterns that indicate threats, and the business impact of technical events.
Talk to DBiz.ai about building a unified AI-driven monitoring framework that eliminates blind spots, accelerates secure response, and transforms operational telemetry into strategic resilience. Your monitoring infrastructure should reduce risk, not create it.
Frequently Asked Questions
What is unified monitoring?
Unified monitoring consolidates telemetry from all operational domains (applications, infrastructure, security, network, cloud) into a single platform that correlates signals, identifies patterns, and provides complete context for every incident. Unlike fragmented monitoring where each team uses separate tools, unified monitoring creates a shared operational intelligence layer accessible to all stakeholders.
How does fragmented monitoring create security risks?
Fragmented monitoring creates blind spots that attackers exploit. Sophisticated threats generate signals across multiple systems. When monitoring tools don't correlate these signals, each anomaly appears minor or normal. By the time human analysts manually correlate events from different systems, attackers have achieved their objectives. Unified monitoring automatically correlates cross-domain signals to identify attack patterns in real-time.
How does AI improve observability?
AI improves observability by learning normal behavior patterns for each service, user, and process. It detects contextual anomalies that static thresholds miss. It correlates related events across systems to identify root causes and attack patterns. It suppresses noise by filtering out false positives and low-priority alerts. It predicts issues before they escalate by recognizing degradation patterns from historical incidents.
What is dashboard fatigue in IT operations?
Dashboard fatigue occurs when teams must monitor 10+ separate dashboards across different tools to understand system health and respond to incidents. Constantly switching between dashboards, manually correlating data, and trying to determine which alerts matter creates cognitive overload and response delays. Teams spend more time managing monitoring tools than deriving value from the data.
How can unified monitoring reduce incident response time?
Unified monitoring reduces incident response time through several mechanisms: automatic correlation eliminates investigation time, clear ownership assignment eliminates handoff delays, complete context reduces troubleshooting time, business-impact prioritization focuses teams on critical issues first, and automated playbooks handle common scenarios without human intervention. Organizations typically see 30-50% improvement in mean time to respond.


